BYOD security that protects the business and the person.
A modern alternative to MDM designed for MSPs. Fast to deploy, easy to manage, and designed for users.

Why traditional MDM falls short for BYOD
A better approach to BYOD security
Aura’s solution combines our award-winning consumer protection with seamless, MSP-friendly deployment—eliminating headaches by balancing device security with employee privacy.
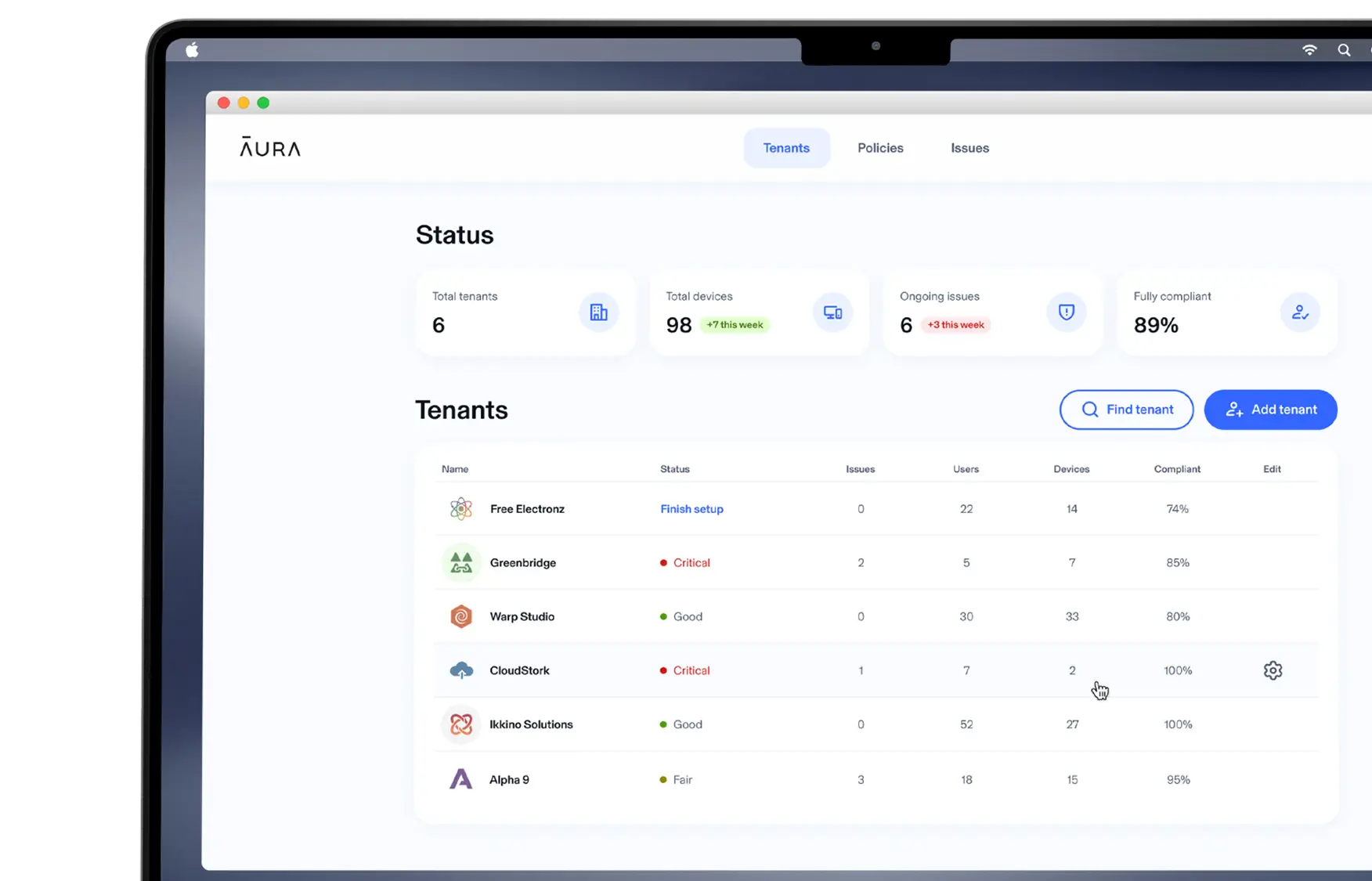
For MSPs
BYOD security that’s fast to deploy, easy to manage, and adopted by employees.
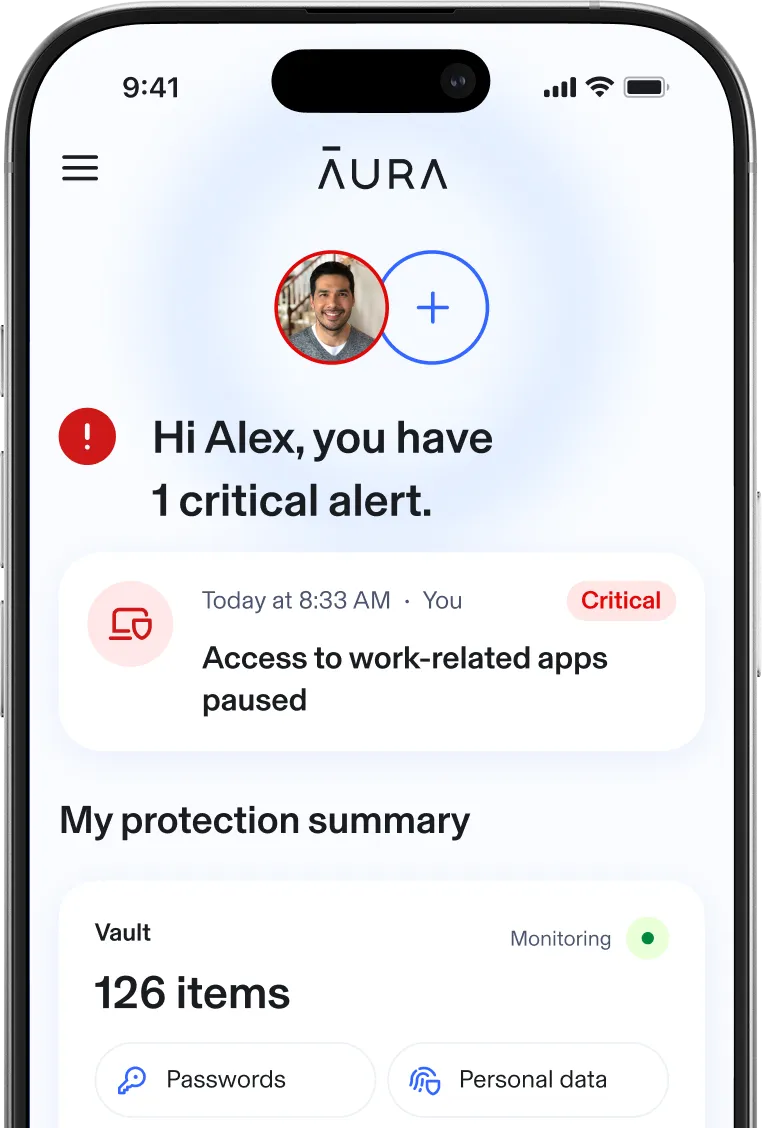
For employees
All-in-one security suite protecting both work and personal data—built to put privacy first.
Why MSPs choose Aura Business
- Fast deployment
Eliminate device enrollment and policy complexity.
- Effortless management
View everything from one lightweight console.
- Privacy-first design
Secures without intrusive device control or tracking.
- All-in-one protection
Help protect the person behind the device, not just the device.
- Increase adoption and trust
Employees are more willing to enroll when their privacy is respected.‡
- Revenue growth
Add new, high-margin protection services for clients.
Modern BYOD security vs. legacy MDM
Aura | Traditional MDM | |
|---|---|---|
Security model | Identity-centric (protects personal + work data) | Device-centric (locks down hardware) |
Privacy impact | Low: no visibility into personal data
or apps | High: invasive visibility into user activity |
Deployment | Lightweight install, zero-touch provisioning | Complex agent enrollment |
Management | Simple dashboard, no constant oversight | Continuous monitoring &
policy enforcement |
Protection coverage | All-in-one protection — identity, passwords, PII, scams, fraud | Basic device compliance |
User experience | Light-touch, benefits the user | Controlling, invasive |





